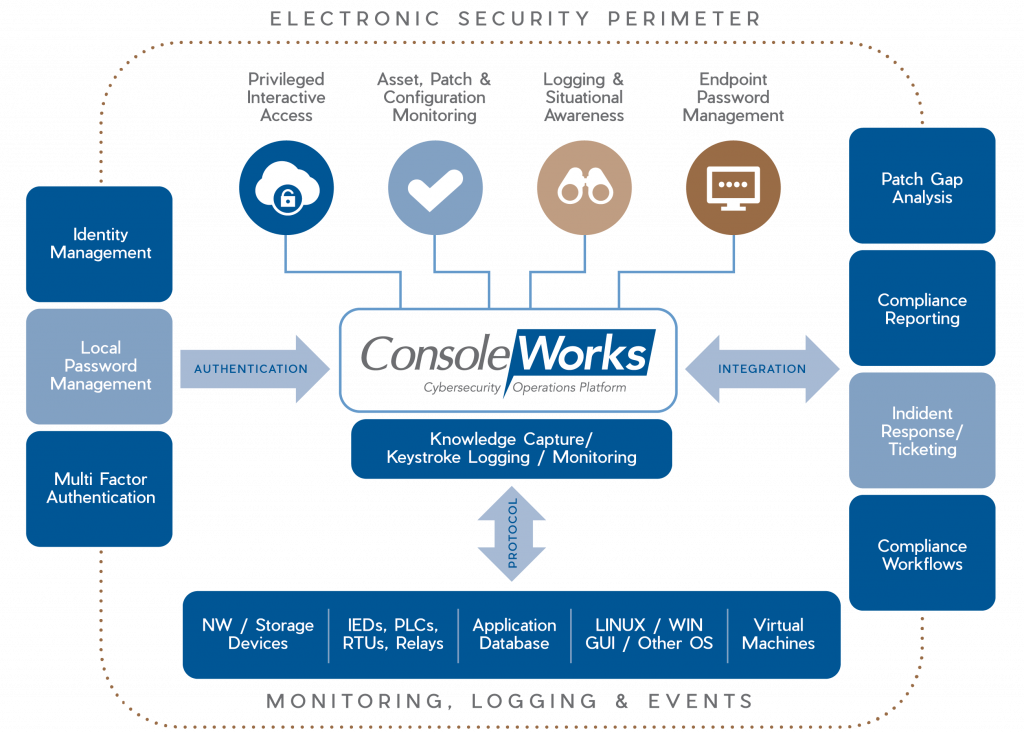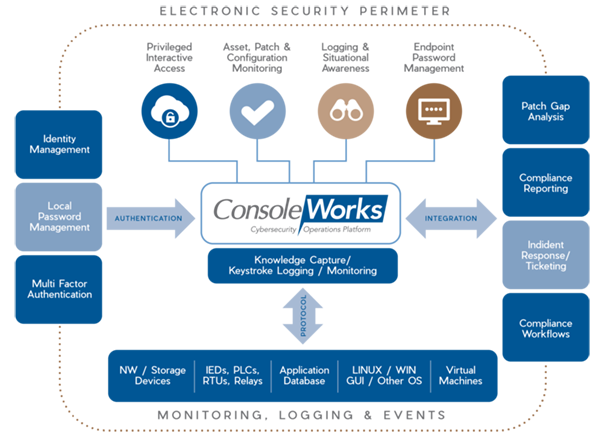
Privileged Interactive Access – ConsoleWorks controls access by allocating specific permissions/ privileges to a user based on the ConsoleWorks Role-Based Access Control (RBAC) permission model. The permission model specifies which assets a user may access and at what level of privilege they may access those systems. ConsoleWorks supports command-by-command privilege grants for absolute control over electronic access.
The ConsoleWorks solution supports integration with an IAM solution and supports RBAC from an Active Directory server. The product was designed with the open ability to integrate its authorization/ authentication services with other technologies, as well.
In addition to command line sessions, ConsoleWorks has the ability to capture complete recording and playback capabilities for privileged user sessions, across RDP/VNC and even web applications. Users gain a complete, detailed account of what happened on sensitive systems, and who performed a specific activity.
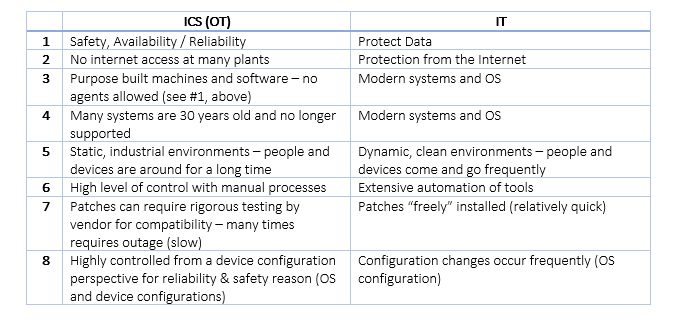
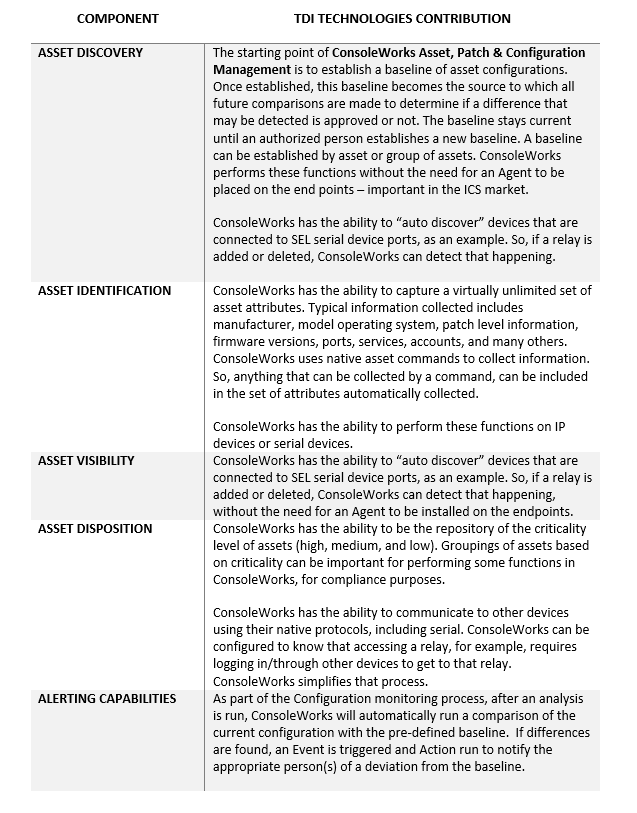
Asset, Patch & Configuration Monitoring – The overriding purpose of configuration monitoring and management is to maintain asset configurations at a known state that have the highest level of security. ConsoleWorks automates the collection, comparison, alert/notification and auditing of any changes to configurations, eliminating the majority of human errors and minimizing the impact of intentional or unintentional erroneous activity.
Endpoint Password Management – From one central location, ConsoleWorks can be configured to schedule automatic password changes and set reset date warnings to meet compliance standards. Operationally, it can recover or change a password securely. When passwords are changed or recovered (for example, in the event of an emergency), notifications can be configured warning the appropriate personnel that it has occurred. The ability to change passwords on demand are controlled through ConsoleWorks granular Access Control Rules.
Logging & Situational Awareness (Logging and Monitoring) – ConsoleWorks can monitor and manage almost any application or infrastructure interface – including routers, switches, servers, firewalls, virtual machines, PLCs, RTUs, appliances, applications and networks – to provide the most comprehensive record possible.
Event Monitoring – ConsoleWorks watches for messages, or Events, in the data streams of all the devices and applications it manages. When ConsoleWorks detects an Event, it alerts the appropriate personnel in real time, records the circumstances, and automatically performs the default or customer-configured response(s). Users are able to respond to the device or application error condition and immediately view the vendor-supplied explanation along with steps required to resolve the issue.
Logging & Log File Aggregation – ConsoleWorks monitors the asset logs in the context of all other managed applications or hardware. Its ability to aggregate error conditions across all log files enables users to view multiple log files, in context, to help in root cause analysis. In many cases, issues have been resolved before other solutions have been notified that an Event has occurred.
Keystroke Logging and Best Practices – ConsoleWorks captures the steps taken for Event remediation down to the keystroke, enabling any ConsoleWorks user to leverage in-house past experience and acquire proven solutions faster. In this way, ConsoleWorks builds the business’s data warehouse of intellectual property related to the problem resolution.
Proof of Compliance – ConsoleWorks produces, aggregates and summarizes audit logs that record user activities, exceptions, and information security events. Log files are digitally secured (line-by-line) for each asset, operating system, application, etc. as they are written, allowing detection of line deletion, insertion or modification.