ConsoleWorks REACT
Risk Evaluation and Assessment for Cyber Threats
ConsoleWorks REACT enables organizations to define Controls used to continually Assess user behavior and asset status to identify and Report operational and cyber risks – directing users to the highest Priorities for Response and Remediation
ConsoleWorks REACT enhances the organization’s overall cybersecurity posture by providing a unified framework for defining security controls used to identify, mitigate and manage cyber risk, enabling users to proactively respond and prioritize security threats based on their potential impact.
The value of risk assessment lies in its ability to empower organizations with actionable intelligence, enabling them to make informed decisions, enhance operational resilience, and safeguard critical assets.
By monitoring and assessing commands issued by users organizations can identify and mitigate potential risks associated with unauthorized or malicious activities, detect anomalies, unusual command sequences or suspicious behavior that may pose a threat to operational integrity.
By leveraging external sources, organizations gain access to a vast array of real-time and contextual information about emerging cyber threats, attack vectors, and malicious activities, enhancing the organization’s ability to identify and respond to potential threats.
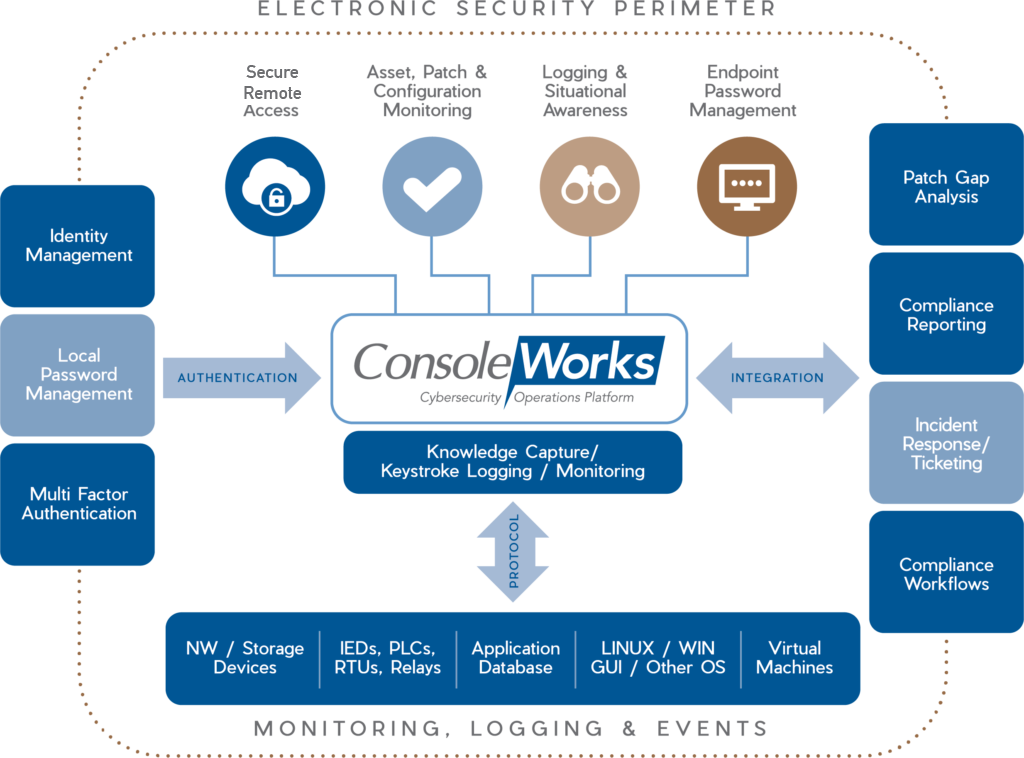
ConsoleWorks REACT embodies the core principles of Zero Trust security, “never trust, always verify”. As the centralized human response and access control, logging, configuration monitoring, endpoint password management solution, our platform offers robust control over user access to essential resources for managing critical infrastructure operations.
By integrating the assessment of user risk factors, such as roles, access privileges, and behavioral patterns, with the assessment of asset risk factors, including vulnerabilities and security configurations, ConsoleWorks REACT delivers a holistic view of the overall cyber and operational risk landscape.
Integration of threat and risk technologies, combined with an understanding of human context and asset operational state, enables organizations to swiftly identify and mitigate potential security breaches and operational vulnerabilities.
Command sequence monitoring is used to monitor a user’s session to determine whether that session activity is increasingly risk based on the sequence or frequency of commands being entered.
Understanding an asset’s impact, criticality and operational state, including threats, enables organizations to swiftly identify and mitigate potential security breaches.
In ConsoleWorks REACT, command control rules can be defined for an asset type for specific users or groups of users. Command sequence monitoring is used to monitor a user’s session to determine whether that session activity is increasingly risk based on the sequence or frequency of commands being entered.
The result is an overall user or interactive user session value based on the potential for compromise to the asset.
ConsoleWorks provides a range of methods to define and monitor system security settings, including monitoring system configurations for overall security settings, firewall changes, and other compliance- and security-related issues, and patch application monitoring. If differences are found, ConsoleWorks provides notification for investigation. The result is an overall specific system or group of systems value based on the potential for compromise.
ConsoleWorks REACT uses input from common threat detection technologies to help identify and assess the likelihood and potential impact of various cyber threats, such as malware or phishing attacks.
An asset can be assigned an impact level depending on the impact that asset has to an organization’s business if compromised.
An asset can be assigned a criticality. A value can be assigned to an asset based on its criticality to the business.
Certain employees may have standard workdays. Activity performed outside of those days could be an indication of nefarious activity by a user.
Certain employees may have standard work hours. Activity performed outside of those hours could be an indication of nefarious activity by a user.
A privileged user's role in the organization can have a direct correlation to the amount of risk associated with the user. A user who has "administrative" access to numerous critical assets may be considered a high-risk user. Alternatively, a new employee may also be considered high risk due to lack of experience.
Unique to ConsoleWorks is the ability to specify extremely granular access control rules to ensure least privilege and user access control rules for specified times. Vendors and contractors could also be assigned an impact level appropriate for either their non-employee status or the potential impact their work may introduce.
ConsoleWorks REACT integrates with the National Vulnerability Database (NVD) to help identify and assess the likelihood and potential impact of vulnerabilities in the organization’s systems, such as outdated software.
In today’s landscape, cyber risks are a critical concern for organizations of all sizes and industries. Cyber-attacks can have significant consequences, including financial losses, reputational damage, and legal liability.
Join us on October 18th where we’re going to show how ConsoleWorks REACT can help centralize and automate your cyber risk assessment for proactive response.